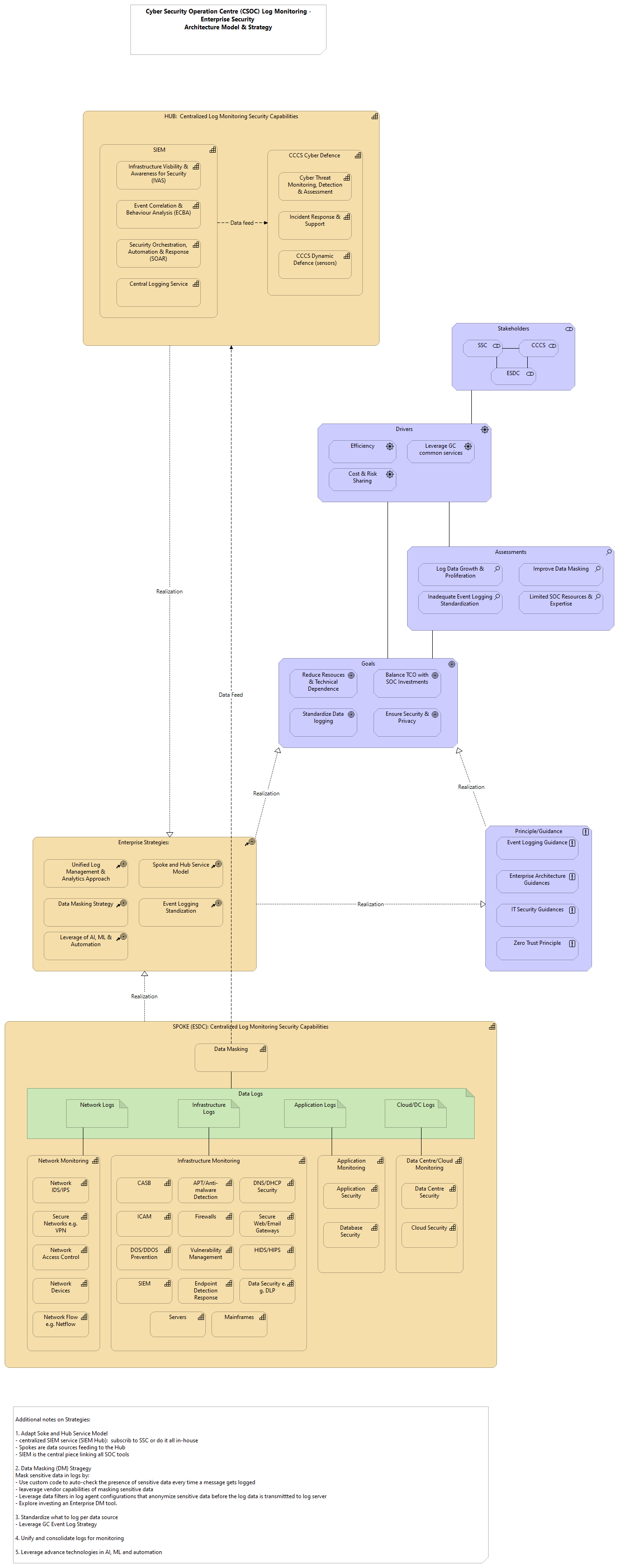
| |
|
Enterprise Strategies: |
Event Logging Standization |
| |
|
Enterprise Strategies: |
Unified Log Management & Analytics Approach |
| Realization |
|
Enterprise Strategies: |
Goals |
| |
|
Enterprise Strategies: |
Data Masking Strategy |
| Realization |
|
Enterprise Strategies: |
Principle/Guidance |
| |
|
Enterprise Strategies: |
Leverage of AI, ML & Automation |
| |
|
Enterprise Strategies: |
Spoke and Hub Service Model |
| |
|
Drivers |
Efficiency |
| |
|
Drivers |
Leverage GC common services |
| |
|
Drivers |
Goals |
| |
|
Drivers |
Assessments |
| |
|
Drivers |
Cost & Risk Sharing |
| |
|
Assessments |
Log Data Growth & Proliferation |
| |
|
Assessments |
Inadequate Event Logging Standardization |
| |
|
Assessments |
Limited SOC Resources & Expertise |
| |
|
Assessments |
Improve Data Masking |
| |
|
Assessments |
Goals |
| |
|
Goals |
Balance TCO with SOC Investments |
| |
|
Goals |
Ensure Security & Privacy |
| |
|
Goals |
Reduce Resouces & Technical Dependence |
| |
|
Goals |
Standardize Data logging |
| |
|
Stakeholders |
ESDC |
| |
|
Stakeholders |
SSC |
| |
|
Stakeholders |
Drivers |
| |
|
Stakeholders |
ESDC |
| |
|
SSC |
CCCS |
| |
|
ESDC |
CCCS |
| |
|
ESDC |
SSC |
| |
|
SPOKE (ESDC): Centralized Log Monitoring Security Capabilities |
Data Masking |
| |
|
SPOKE (ESDC): Centralized Log Monitoring Security Capabilities |
Data Centre/Cloud Monitoring |
| Realization |
|
SPOKE (ESDC): Centralized Log Monitoring Security Capabilities |
Enterprise Strategies: |
| |
|
SPOKE (ESDC): Centralized Log Monitoring Security Capabilities |
Application Monitoring |
| |
|
SPOKE (ESDC): Centralized Log Monitoring Security Capabilities |
Infrastructure Monitoring |
| |
|
SPOKE (ESDC): Centralized Log Monitoring Security Capabilities |
Network Monitoring |
| |
|
Network Monitoring |
Network Devices |
| |
|
Network Monitoring |
Network IDS/IPS |
| |
|
Network Monitoring |
Secure Networks e.g. VPN |
| |
|
Network Monitoring |
Network Access Control |
| |
|
Network Monitoring |
Network Flow e.g. Netflow |
| |
|
Infrastructure Monitoring |
DOS/DDOS Prevention |
| |
|
Infrastructure Monitoring |
Data Security e.g. DLP |
| |
|
Infrastructure Monitoring |
DNS/DHCP Security |
| |
|
Infrastructure Monitoring |
ICAM |
| |
|
Infrastructure Monitoring |
Secure Web/Email Gateways |
| |
|
Infrastructure Monitoring |
CASB |
| |
|
Infrastructure Monitoring |
Vulnerability Management |
| |
|
Infrastructure Monitoring |
Firewalls |
| |
|
Infrastructure Monitoring |
Endpoint Detection Response |
| |
|
Infrastructure Monitoring |
Servers |
| |
|
Infrastructure Monitoring |
HIDS/HIPS |
| |
|
Infrastructure Monitoring |
APT/Anti-malware Detection |
| |
|
Infrastructure Monitoring |
Mainframes |
| |
|
Infrastructure Monitoring |
SIEM |
| |
|
Application Monitoring |
Database Security |
| |
|
Application Monitoring |
Application Security |
| |
|
Data Centre/Cloud Monitoring |
Data Centre Security |
| |
|
Data Centre/Cloud Monitoring |
Cloud Security |
| Data Feed |
|
Data Masking |
HUB: Centralized Log Monitoring Security Capabilities |
| |
|
Data Logs |
Application Logs |
| |
|
Data Logs |
Cloud/DC Logs |
| |
|
Data Logs |
Data Masking |
| |
|
Data Logs |
Network Logs |
| |
|
Data Logs |
Infrastructure Logs |
| |
|
Network Logs |
Network Monitoring |
| |
|
Infrastructure Logs |
Infrastructure Monitoring |
| |
|
Application Logs |
Application Monitoring |
| |
|
Cloud/DC Logs |
Data Centre/Cloud Monitoring |
| Realization |
|
Principle/Guidance |
Goals |
| |
|
HUB: Centralized Log Monitoring Security Capabilities |
CCCS Cyber Defence |
| |
|
HUB: Centralized Log Monitoring Security Capabilities |
SIEM |
| Realization |
|
HUB: Centralized Log Monitoring Security Capabilities |
Enterprise Strategies: |
| Data feed |
|
SIEM |
CCCS Cyber Defence |