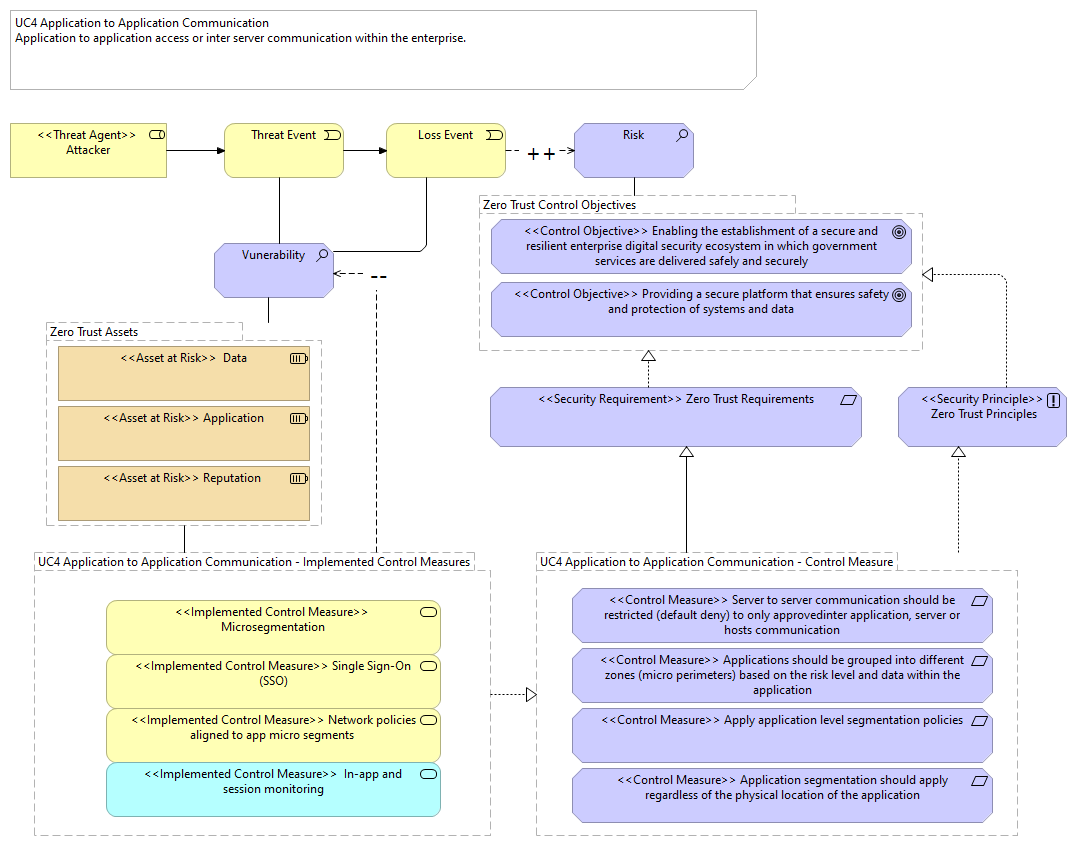
| |
|
UC4 Application to Application Communication - Implemented Control Measures |
<<Implemented Control Measure>> Network policies aligned to app micro segments |
| |
|
UC4 Application to Application Communication - Implemented Control Measures |
<<Implemented Control Measure>> In-app and session monitoring |
| |
|
UC4 Application to Application Communication - Implemented Control Measures |
<<Implemented Control Measure>> Single Sign-On (SSO) |
| |
|
UC4 Application to Application Communication - Implemented Control Measures |
<<Implemented Control Measure>> Microsegmentation |
| |
|
UC4 Application to Application Communication - Implemented Control Measures |
Vunerability |
| |
|
UC4 Application to Application Communication - Implemented Control Measures |
UC4 Application to Application Communication - Control Measure |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Security Requirement>> Zero Trust Requirements |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Security Principle>> Zero Trust Principles |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Application segmentation should apply regardless of the physical location of the application |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Apply application level segmentation policies |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Applications should be grouped into different zones (micro perimeters) based on the risk level and data within the application |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Server to server communication should be restricted (default deny) to only approvedinter application, server or hosts communication |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Reputation |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Application |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Data |
| |
|
Zero Trust Assets |
UC4 Application to Application Communication - Implemented Control Measures |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Providing a secure platform that ensures safety and protection of systems and data |
| |
|
Zero Trust Control Objectives |
Risk |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Enabling the establishment of a secure and resilient enterprise digital security ecosystem in which government services are delivered safely and securely |
| |
|
<<Threat Agent>> Attacker |
Threat Event |
| |
|
Threat Event |
Vunerability |
| |
|
Threat Event |
Loss Event |
| |
|
Loss Event |
Vunerability |
| |
|
Loss Event |
Risk |
| |
|
Vunerability |
Zero Trust Assets |
| |
|
<<Security Principle>> Zero Trust Principles |
Zero Trust Control Objectives |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Zero Trust Control Objectives |