| |
|
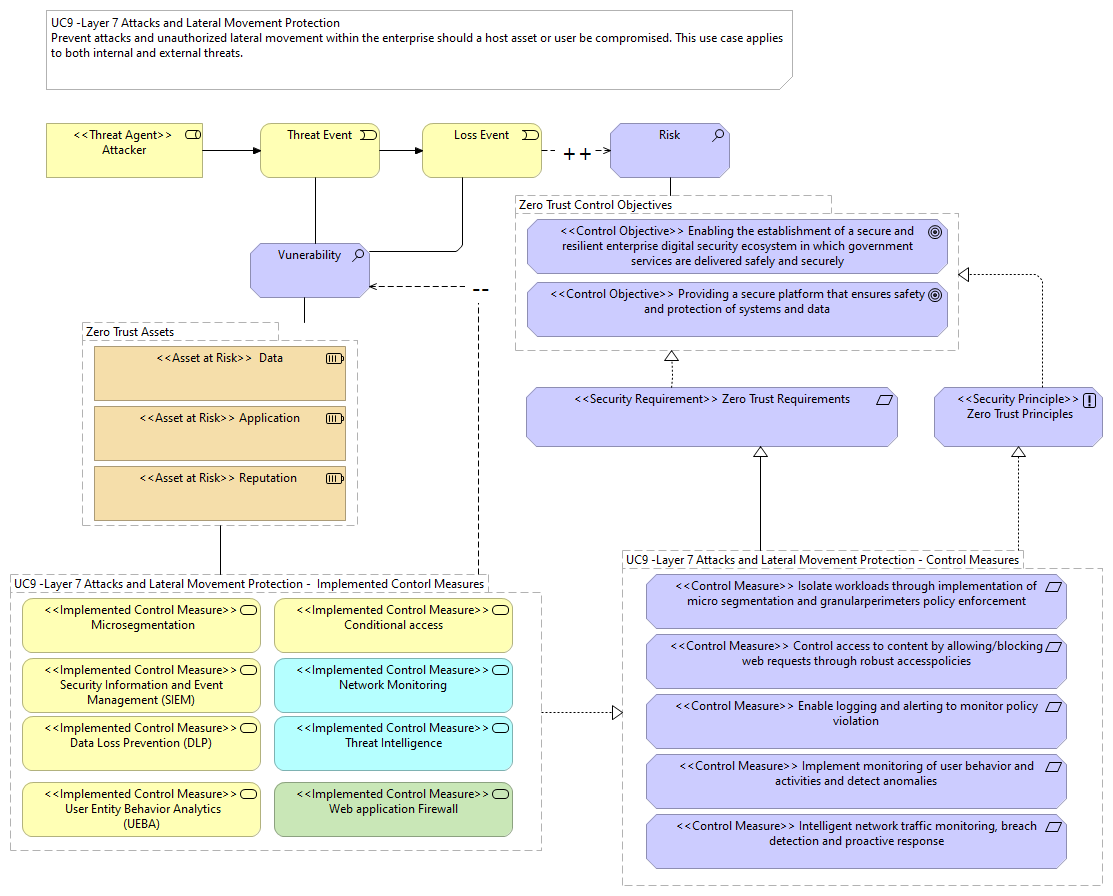
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> User Entity Behavior Analytics (UEBA) |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Threat Intelligence |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Data Loss Prevention (DLP) |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Microsegmentation |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Web application Firewall |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Security Information and Event Management (SIEM) |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Conditional access |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
<<Implemented Control Measure>> Network Monitoring |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
Vunerability |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Implement monitoring of user behavior and activities and detect anomalies |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Enable logging and alerting to monitor policy violation |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Isolate workloads through implementation of micro segmentation and granularperimeters policy enforcement |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Control access to content by allowing/blocking web requests through robust accesspolicies |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Intelligent network traffic monitoring, breach detection and proactive response |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Security Requirement>> Zero Trust Requirements |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Security Principle>> Zero Trust Principles |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Reputation |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Data |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Application |
| |
|
Zero Trust Assets |
UC9 -Layer 7 Attacks and Lateral Movement Protection - Implemented Contorl Measures |
| |
|
Zero Trust Control Objectives |
Risk |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Providing a secure platform that ensures safety and protection of systems and data |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Enabling the establishment of a secure and resilient enterprise digital security ecosystem in which government services are delivered safely and securely |
| |
|
<<Threat Agent>> Attacker |
Threat Event |
| |
|
Threat Event |
Vunerability |
| |
|
Threat Event |
Loss Event |
| |
|
Loss Event |
Vunerability |
| |
|
Loss Event |
Risk |
| |
|
Vunerability |
Zero Trust Assets |
| |
|
<<Security Principle>> Zero Trust Principles |
Zero Trust Control Objectives |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Zero Trust Control Objectives |