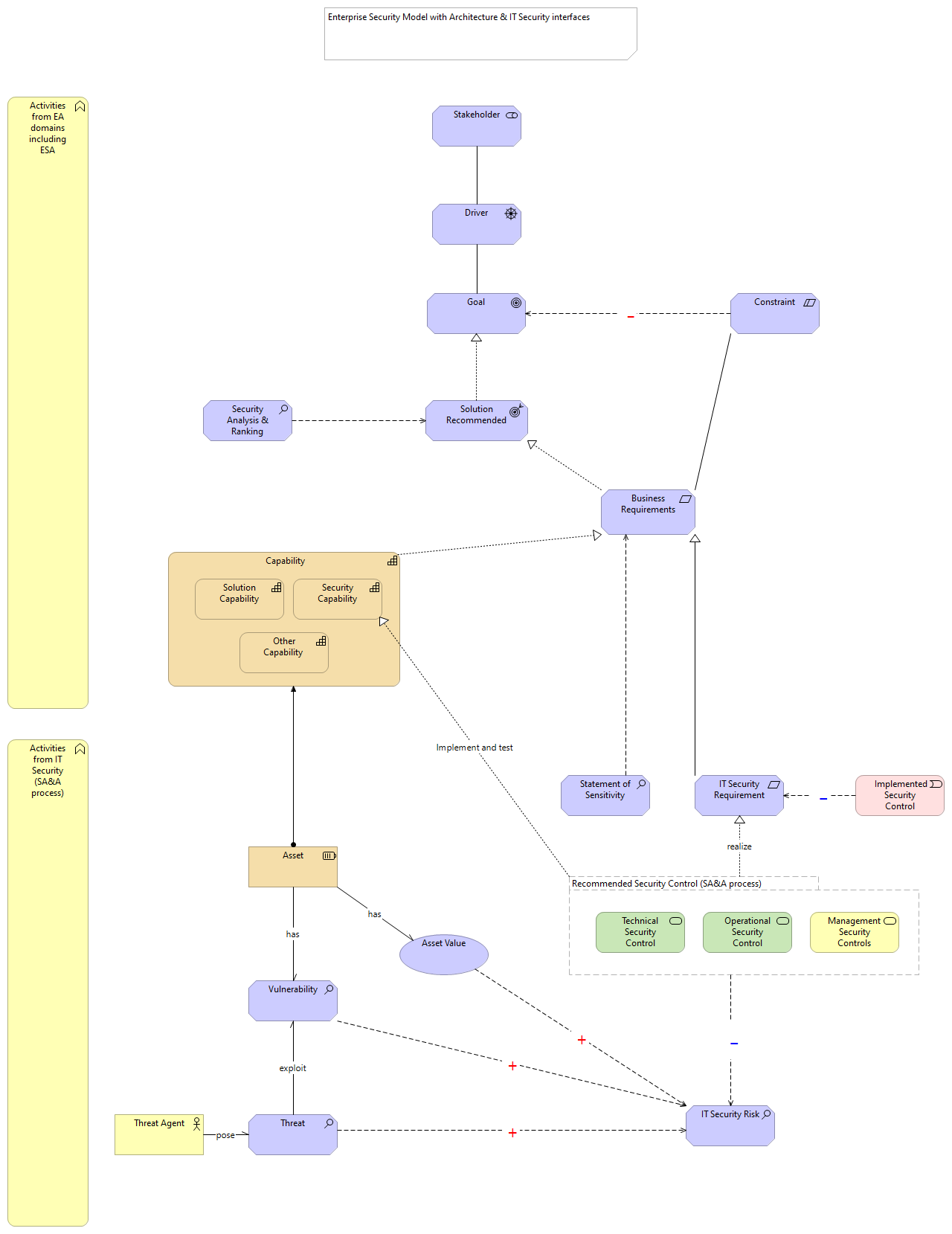
| pose |
|
Threat Agent |
Threat |
| |
|
Vulnerability |
IT Security Risk |
| |
|
Asset Value |
IT Security Risk |
| exploit |
|
Threat |
Vulnerability |
| |
|
Threat |
IT Security Risk |
| |
|
Recommended Security Control (SA&A process) |
Management Security Controls |
| |
|
Recommended Security Control (SA&A process) |
IT Security Risk |
| Implement and test |
|
Recommended Security Control (SA&A process) |
Security Capability |
| realize |
|
Recommended Security Control (SA&A process) |
IT Security Requirement |
| |
|
Recommended Security Control (SA&A process) |
Technical Security Control |
| |
|
Recommended Security Control (SA&A process) |
Operational Security Control |
| |
|
Implemented Security Control |
IT Security Requirement |
| |
|
Driver |
Goal |
| |
|
Business Requirements |
Solution Recommended |
| |
|
Constraint |
Business Requirements |
| |
|
Constraint |
Goal |
| has |
|
Asset |
Asset Value |
| |
|
Asset |
Capability |
| has |
|
Asset |
Vulnerability |
| |
|
Capability |
Business Requirements |
| |
|
Capability |
Solution Capability |
| |
|
Capability |
Other Capability |
| |
|
Capability |
Security Capability |
| |
|
IT Security Requirement |
Business Requirements |
| |
|
Stakeholder |
Driver |
| |
|
Solution Recommended |
Goal |
| |
|
Statement of Sensitivity |
Business Requirements |
| |
|
Security Analysis & Ranking |
Solution Recommended |