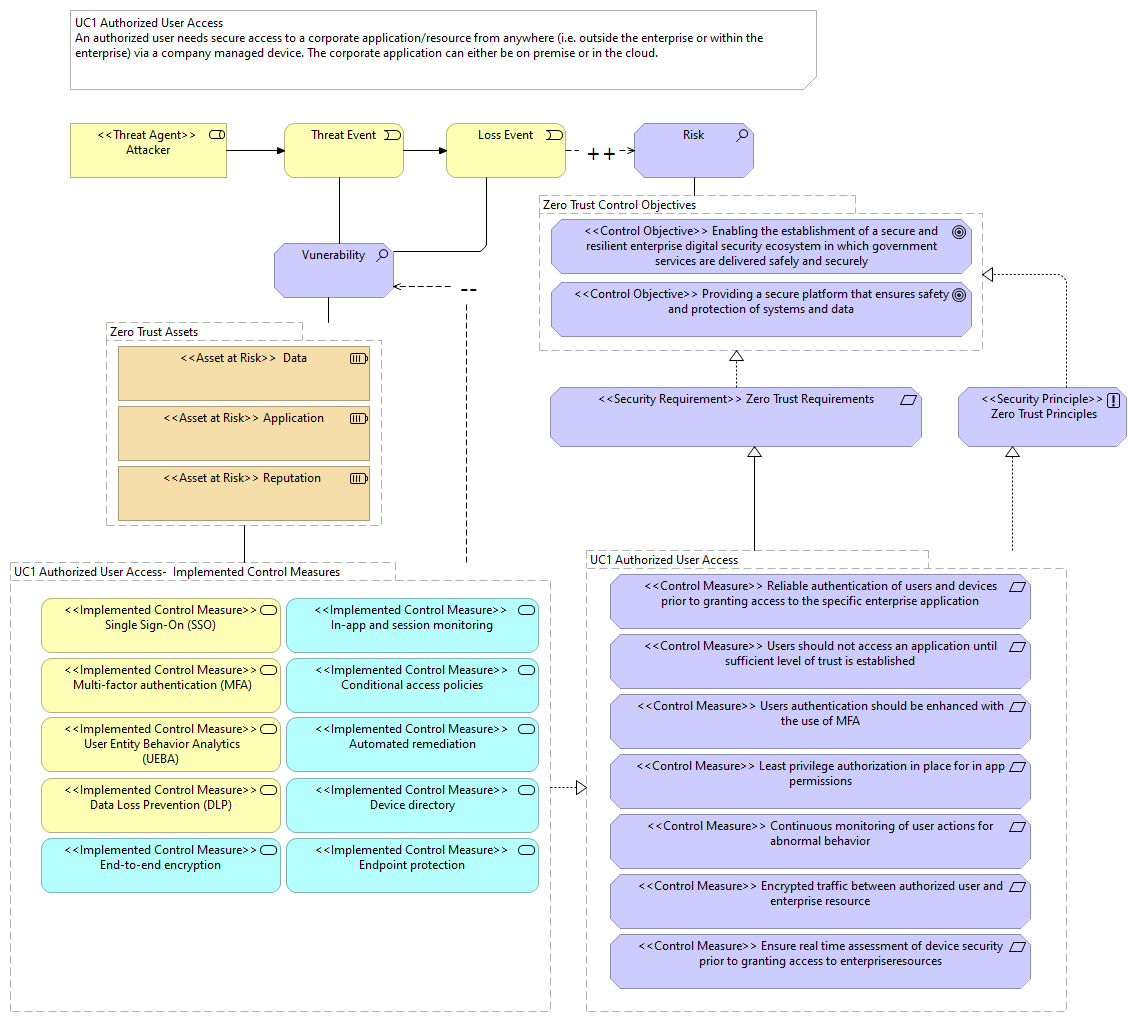
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Endpoint protection |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Automated remediation |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Device directory |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Single Sign-On (SSO) |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Multi-factor authentication (MFA) |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Conditional access policies |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> In-app and session monitoring |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> User Entity Behavior Analytics (UEBA) |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> End-to-end encryption |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
<<Implemented Control Measure>> Data Loss Prevention (DLP) |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
UC1 Authorized User Access |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
Zero Trust Assets |
| |
|
UC1 Authorized User Access- Implemented Control Measures |
Vunerability |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Reputation |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Application |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Data |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Providing a secure platform that ensures safety and protection of systems and data |
| |
|
Zero Trust Control Objectives |
Risk |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Enabling the establishment of a secure and resilient enterprise digital security ecosystem in which government services are delivered safely and securely |
| |
|
<<Threat Agent>> Attacker |
Threat Event |
| |
|
Threat Event |
Loss Event |
| |
|
Threat Event |
Vunerability |
| |
|
Loss Event |
Vunerability |
| |
|
Loss Event |
Risk |
| |
|
Vunerability |
Zero Trust Assets |
| |
|
<<Security Principle>> Zero Trust Principles |
Zero Trust Control Objectives |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Zero Trust Control Objectives |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Encrypted traffic between authorized user and enterprise resource |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Users authentication should be enhanced with the use of MFA |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Users should not access an application until sufficient level of trust is established |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Least privilege authorization in place for in app permissions |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Ensure real time assessment of device security prior to granting access to enterpriseresources |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Continuous monitoring of user actions for abnormal behavior |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Reliable authentication of users and devices prior to granting access to the specific enterprise application |
| |
|
UC1 Authorized User Access |
<<Security Requirement>> Zero Trust Requirements |
| |
|
UC1 Authorized User Access |
<<Security Principle>> Zero Trust Principles |