| |
|
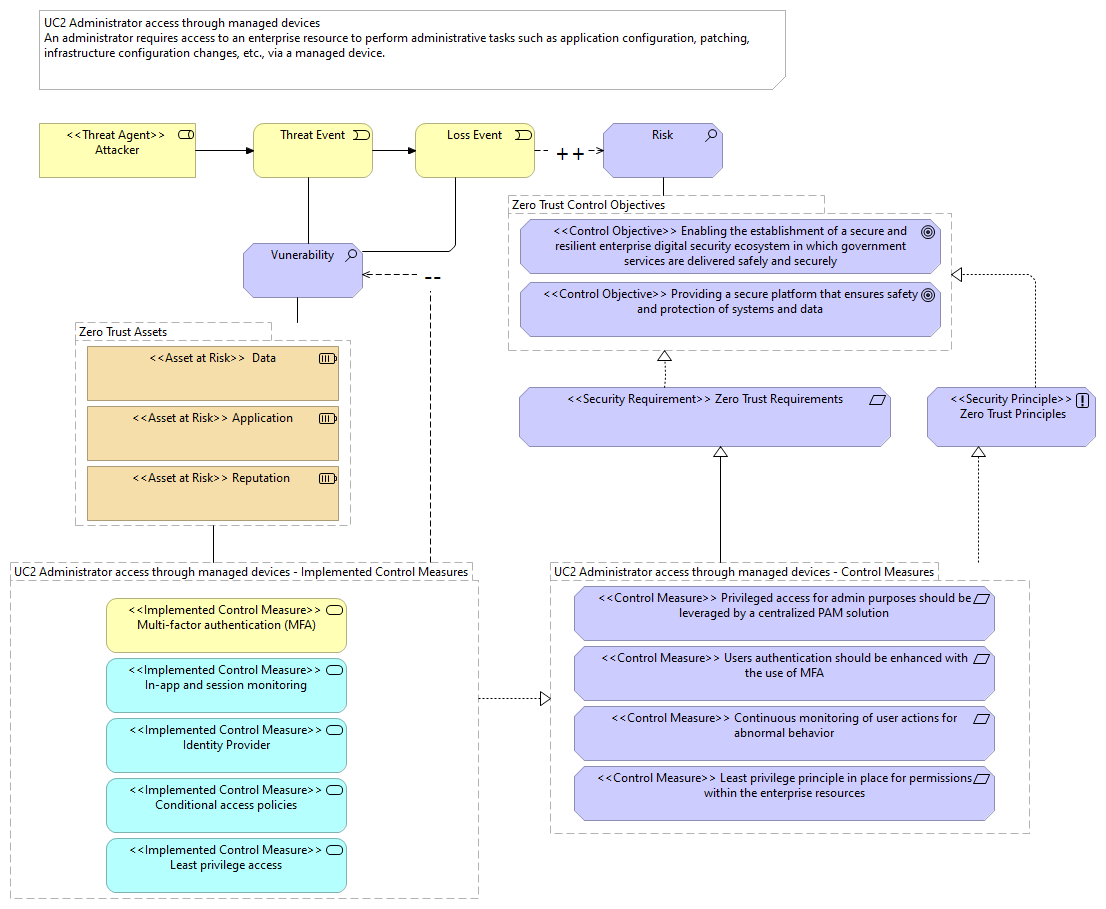
UC2 Administrator access through managed devices - Implemented Control Measures |
<<Implemented Control Measure>> Multi-factor authentication (MFA) |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
<<Implemented Control Measure>> In-app and session monitoring |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
<<Implemented Control Measure>> Identity Provider |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
<<Implemented Control Measure>> Conditional access policies |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
<<Implemented Control Measure>> Least privilege access |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
UC2 Administrator access through managed devices - Control Measures |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
Zero Trust Assets |
| |
|
UC2 Administrator access through managed devices - Implemented Control Measures |
Vunerability |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Privileged access for admin purposes should be leveraged by a centralized PAM solution |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Users authentication should be enhanced with the use of MFA |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Least privilege principle in place for permissions within the enterprise resources |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Continuous monitoring of user actions for abnormal behavior |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Security Requirement>> Zero Trust Requirements |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Security Principle>> Zero Trust Principles |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Data |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Reputation |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Application |
| |
|
Zero Trust Control Objectives |
Risk |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Providing a secure platform that ensures safety and protection of systems and data |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Enabling the establishment of a secure and resilient enterprise digital security ecosystem in which government services are delivered safely and securely |
| |
|
<<Threat Agent>> Attacker |
Threat Event |
| |
|
Threat Event |
Vunerability |
| |
|
Threat Event |
Loss Event |
| |
|
Loss Event |
Vunerability |
| |
|
Loss Event |
Risk |
| |
|
Vunerability |
Zero Trust Assets |
| |
|
<<Security Principle>> Zero Trust Principles |
Zero Trust Control Objectives |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Zero Trust Control Objectives |