| |
|
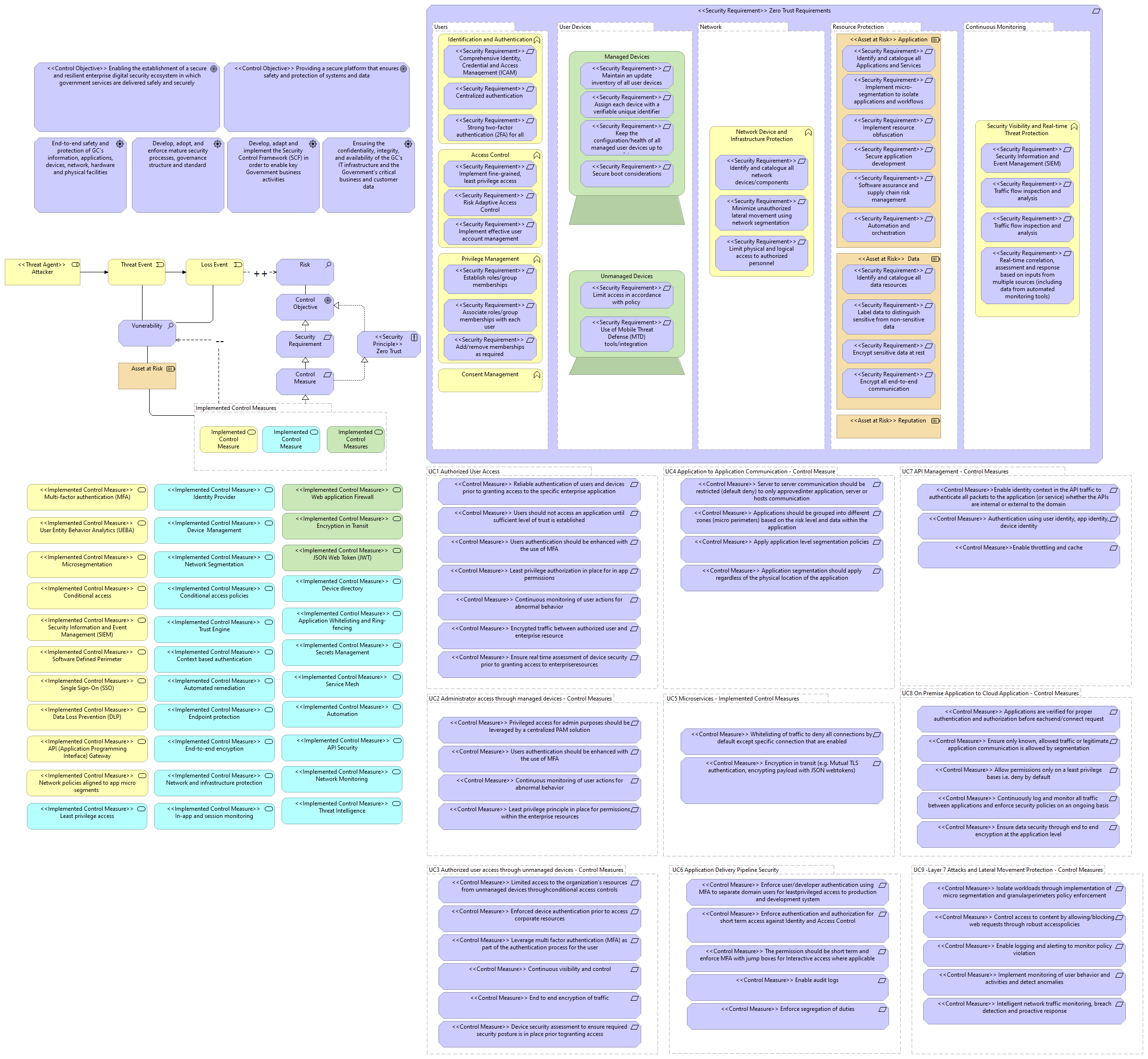
<<Threat Agent>> Attacker |
Threat Event |
| |
|
Threat Event |
Vunerability |
| |
|
Threat Event |
Loss Event |
| |
|
Loss Event |
Vunerability |
| |
|
Loss Event |
Risk |
| |
|
Asset at Risk |
Implemented Control Measures |
| |
|
Vunerability |
Asset at Risk |
| |
|
Control Objective |
Risk |
| |
|
Security Requirement |
Control Objective |
| |
|
<<Security Principle>> Zero Trust Principles |
Control Objective |
| |
|
Control Measure |
<<Security Principle>> Zero Trust Principles |
| |
|
Control Measure |
Security Requirement |
| |
|
Implemented Control Measures |
Implemented Control Measure |
| |
|
Implemented Control Measures |
Implemented Control Measure |
| |
|
Implemented Control Measures |
Implemented Control Measures |
| |
|
Implemented Control Measures |
Control Measure |
| |
|
Implemented Control Measures |
Vunerability |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Users |
| |
|
<<Security Requirement>> Zero Trust Requirements |
User Devices |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Continuous Monitoring |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Network |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Resource Protection |
| |
|
Resource Protection |
<<Asset at Risk>> Data |
| |
|
Resource Protection |
<<Asset at Risk>> Application |
| |
|
Resource Protection |
<<Asset at Risk>> Reputation |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Label data to distinguish sensitive from non-sensitive data |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Encrypt sensitive data at rest |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Identify and catalogue all data resources |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Encrypt all end-to-end communication |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Implement resource obfuscation |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Secure application development |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Software assurance and supply chain risk management |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Identify and catalogue all Applications and Services |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Implement micro-segmentation to isolate applications and workflows |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Automation and orchestration |
| |
|
Continuous Monitoring |
Security Visibility and Real-time Threat Protection |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Traffic flow inspection and analysis |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Traffic flow inspection and analysis |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Real-time correlation, assessment and response based on inputs from multiple sources (including data from automated monitoring tools) |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Security Information and Event Management (SIEM) |
| |
|
Users |
Identification and Authentication |
| |
|
Users |
Privilege Management |
| |
|
Users |
Access Control |
| |
|
Users |
Consent Management |
| |
|
Identification and Authentication |
<<Security Requirement>> Strong two-factor authentication (2FA) for all users, regardless of location |
| |
|
Identification and Authentication |
<<Security Requirement>> Centralized authentication |
| |
|
Identification and Authentication |
<<Security Requirement>> Comprehensive Identity, Credential and Access Management (ICAM) |
| |
|
Privilege Management |
<<Security Requirement>> Associate roles/group memberships with each user |
| |
|
Privilege Management |
<<Security Requirement>> Establish roles/group memberships |
| |
|
Privilege Management |
<<Security Requirement>> Add/remove memberships as required |
| |
|
Access Control |
<<Security Requirement>> Implement fine-grained, least privilege access control |
| |
|
Access Control |
<<Security Requirement>> Risk Adaptive Access Control |
| |
|
Access Control |
<<Security Requirement>> Implement effective user account management procedures |
| |
|
Network |
Network Device and Infrastructure Protection |
| |
|
Network Device and Infrastructure Protection |
<<Security Requirement>> Minimize unauthorized lateral movement using network segmentation |
| |
|
Network Device and Infrastructure Protection |
<<Security Requirement>> Limit physical and logical access to authorized personnel |
| |
|
Network Device and Infrastructure Protection |
<<Security Requirement>> Identify and catalogue all network devices/components |
| |
|
User Devices |
Managed Devices |
| |
|
User Devices |
Unmanaged Devices |
| |
|
Managed Devices |
<<Security Requirement>> Assign each device with a verifiable unique identifier |
| |
|
Managed Devices |
<<Security Requirement>> Secure boot considerations |
| |
|
Managed Devices |
<<Security Requirement>> Keep the configuration/health of all managed user devices up to date |
| |
|
Managed Devices |
<<Security Requirement>> Maintain an update inventory of all user devices |
| |
|
Unmanaged Devices |
<<Security Requirement>> Limit access in accordance with policy |
| |
|
Unmanaged Devices |
<<Security Requirement>> Use of Mobile Threat Defense (MTD) tools/integration |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Isolate workloads through implementation of micro segmentation and granularperimeters policy enforcement |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Implement monitoring of user behavior and activities and detect anomalies |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Intelligent network traffic monitoring, breach detection and proactive response |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Control access to content by allowing/blocking web requests through robust accesspolicies |
| |
|
UC9 -Layer 7 Attacks and Lateral Movement Protection - Control Measures |
<<Control Measure>> Enable logging and alerting to monitor policy violation |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Applications are verified for proper authentication and authorization before eachsend/connect request |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Ensure only known, allowed traffic or legitimate application communication is allowed by segmentation |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Ensure data security through end to end encryption at the application level |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Allow permissions only on a least privilege bases i.e. deny by default |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Continuously log and monitor all traffic between applications and enforce security policies on an ongoing basis |
| |
|
UC7 API Management - Control Measures |
<<Control Measure>> Authentication using user identity, app identity, device identity |
| |
|
UC7 API Management - Control Measures |
<<Control Measure>>Enable throttling and cache |
| |
|
UC7 API Management - Control Measures |
<<Control Measure>>Enable identity context in the API traffic to authenticate all packets to the application (or service) whether the APIs are internal or external to the domain |
| |
|
UC6 Application Delivery Pipeline Security |
<<Control Measure>> The permission should be short term and enforce MFA with jump boxes for Interactive access where applicable |
| |
|
UC6 Application Delivery Pipeline Security |
<<Control Measure>> Enforce segregation of duties |
| |
|
UC6 Application Delivery Pipeline Security |
<<Control Measure>> Enable audit logs |
| |
|
UC6 Application Delivery Pipeline Security |
<<Control Measure>> Enforce user/developer authentication using MFA to separate domain users for leastprivileged access to production and development system |
| |
|
UC6 Application Delivery Pipeline Security |
<<Control Measure>> Enforce authentication and authorization for short term access against Identity and Access Control |
| |
|
UC5 Microservices - Implemented Control Measures |
<<Control Measure>> Encryption in transit (e.g. Mutual TLS authentication, encrypting payload with JSON webtokens) |
| |
|
UC5 Microservices - Implemented Control Measures |
<<Control Measure>> Whitelisting of traffic to deny all connections by default except specific connection that are enabled |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Applications should be grouped into different zones (micro perimeters) based on the risk level and data within the application |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Application segmentation should apply regardless of the physical location of the application |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Apply application level segmentation policies |
| |
|
UC4 Application to Application Communication - Control Measure |
<<Control Measure>> Server to server communication should be restricted (default deny) to only approvedinter application, server or hosts communication |
| |
|
UC3 Authorized user access through unmanaged devices - Control Measures |
<<Control Measure>> Limited access to the organization’s resources from unmanaged devices throughconditional access controls |
| |
|
UC3 Authorized user access through unmanaged devices - Control Measures |
<<Control Measure>> Enforced device authentication prior to access corporate resources |
| |
|
UC3 Authorized user access through unmanaged devices - Control Measures |
<<Control Measure>> End to end encryption of traffic |
| |
|
UC3 Authorized user access through unmanaged devices - Control Measures |
<<Control Measure>> Device security assessment to ensure required security posture is in place prior togranting access |
| |
|
UC3 Authorized user access through unmanaged devices - Control Measures |
<<Control Measure>> Leverage multi factor authentication (MFA) as part of the authentication process for the user |
| |
|
UC3 Authorized user access through unmanaged devices - Control Measures |
<<Control Measure>> Continuous visibility and control |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Privileged access for admin purposes should be leveraged by a centralized PAM solution |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Users authentication should be enhanced with the use of MFA |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Continuous monitoring of user actions for abnormal behavior |
| |
|
UC2 Administrator access through managed devices - Control Measures |
<<Control Measure>> Least privilege principle in place for permissions within the enterprise resources |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Reliable authentication of users and devices prior to granting access to the specific enterprise application |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Users should not access an application until sufficient level of trust is established |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Users authentication should be enhanced with the use of MFA |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Least privilege authorization in place for in app permissions |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Continuous monitoring of user actions for abnormal behavior |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Encrypted traffic between authorized user and enterprise resource |
| |
|
UC1 Authorized User Access |
<<Control Measure>> Ensure real time assessment of device security prior to granting access to enterpriseresources |