| |
|
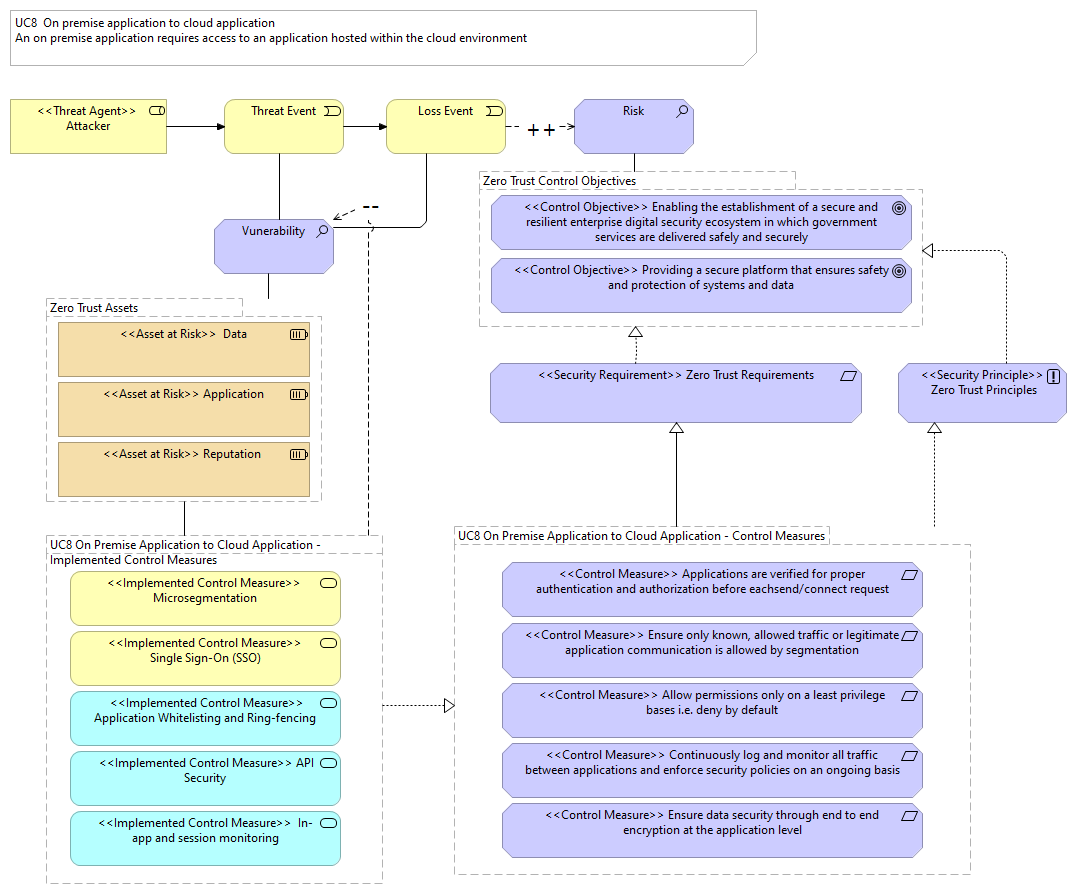
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
<<Implemented Control Measure>> Microsegmentation |
| |
|
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
<<Implemented Control Measure>> API Security |
| |
|
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
<<Implemented Control Measure>> Single Sign-On (SSO) |
| |
|
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
<<Implemented Control Measure>> Application Whitelisting and Ring-fencing |
| |
|
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
<<Implemented Control Measure>> In-app and session monitoring |
| |
|
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
Vunerability |
| |
|
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
UC8 On Premise Application to Cloud Application - Control Measures |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Security Requirement>> Zero Trust Requirements |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Security Principle>> Zero Trust Principles |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Ensure data security through end to end encryption at the application level |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Continuously log and monitor all traffic between applications and enforce security policies on an ongoing basis |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Allow permissions only on a least privilege bases i.e. deny by default |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Ensure only known, allowed traffic or legitimate application communication is allowed by segmentation |
| |
|
UC8 On Premise Application to Cloud Application - Control Measures |
<<Control Measure>> Applications are verified for proper authentication and authorization before eachsend/connect request |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Application |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Reputation |
| |
|
Zero Trust Assets |
<<Asset at Risk>> Data |
| |
|
Zero Trust Assets |
UC8 On Premise Application to Cloud Application - Implemented Control Measures |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Enabling the establishment of a secure and resilient enterprise digital security ecosystem in which government services are delivered safely and securely |
| |
|
Zero Trust Control Objectives |
<<Control Objective>> Providing a secure platform that ensures safety and protection of systems and data |
| |
|
Zero Trust Control Objectives |
Risk |
| |
|
<<Threat Agent>> Attacker |
Threat Event |
| |
|
Threat Event |
Vunerability |
| |
|
Threat Event |
Loss Event |
| |
|
Loss Event |
Risk |
| |
|
Loss Event |
Vunerability |
| |
|
Vunerability |
Zero Trust Assets |
| |
|
<<Security Principle>> Zero Trust Principles |
Zero Trust Control Objectives |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Zero Trust Control Objectives |