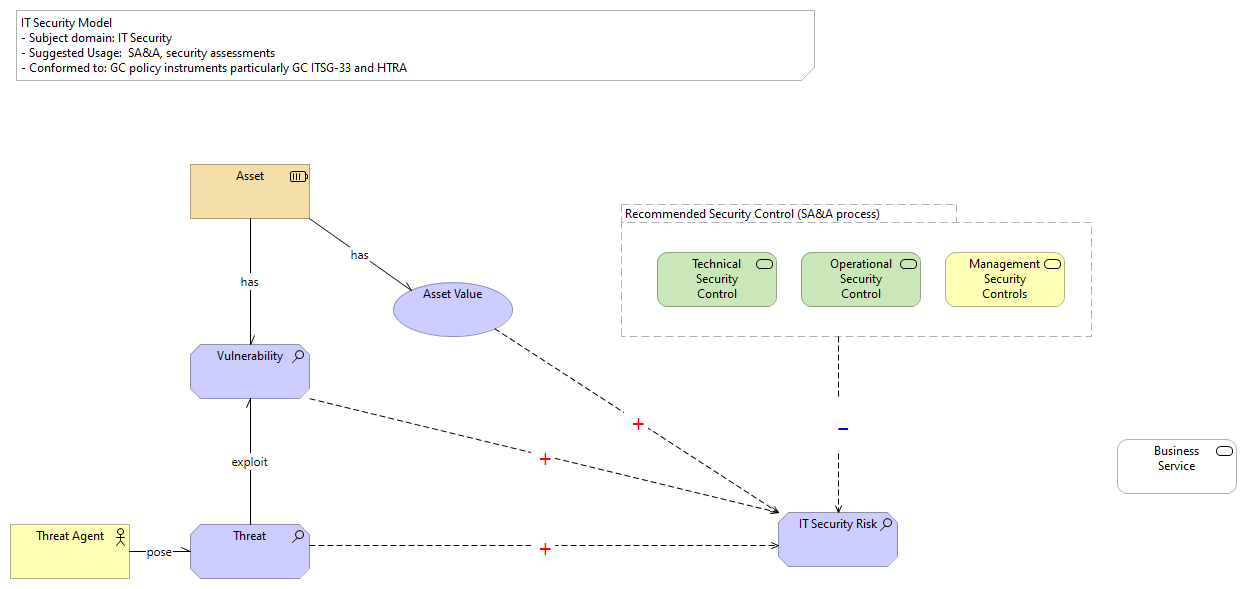
| pose |
|
Threat Agent |
Threat |
| |
|
Vulnerability |
IT Security Risk |
| |
|
Asset Value |
IT Security Risk |
| exploit |
|
Threat |
Vulnerability |
| |
|
Threat |
IT Security Risk |
| |
|
Recommended Security Control (SA&A process) |
Operational Security Control |
| |
|
Recommended Security Control (SA&A process) |
Technical Security Control |
| |
|
Recommended Security Control (SA&A process) |
Management Security Controls |
| |
|
Recommended Security Control (SA&A process) |
IT Security Risk |
| has |
|
Asset |
Vulnerability |
| has |
|
Asset |
Asset Value |