| |
|
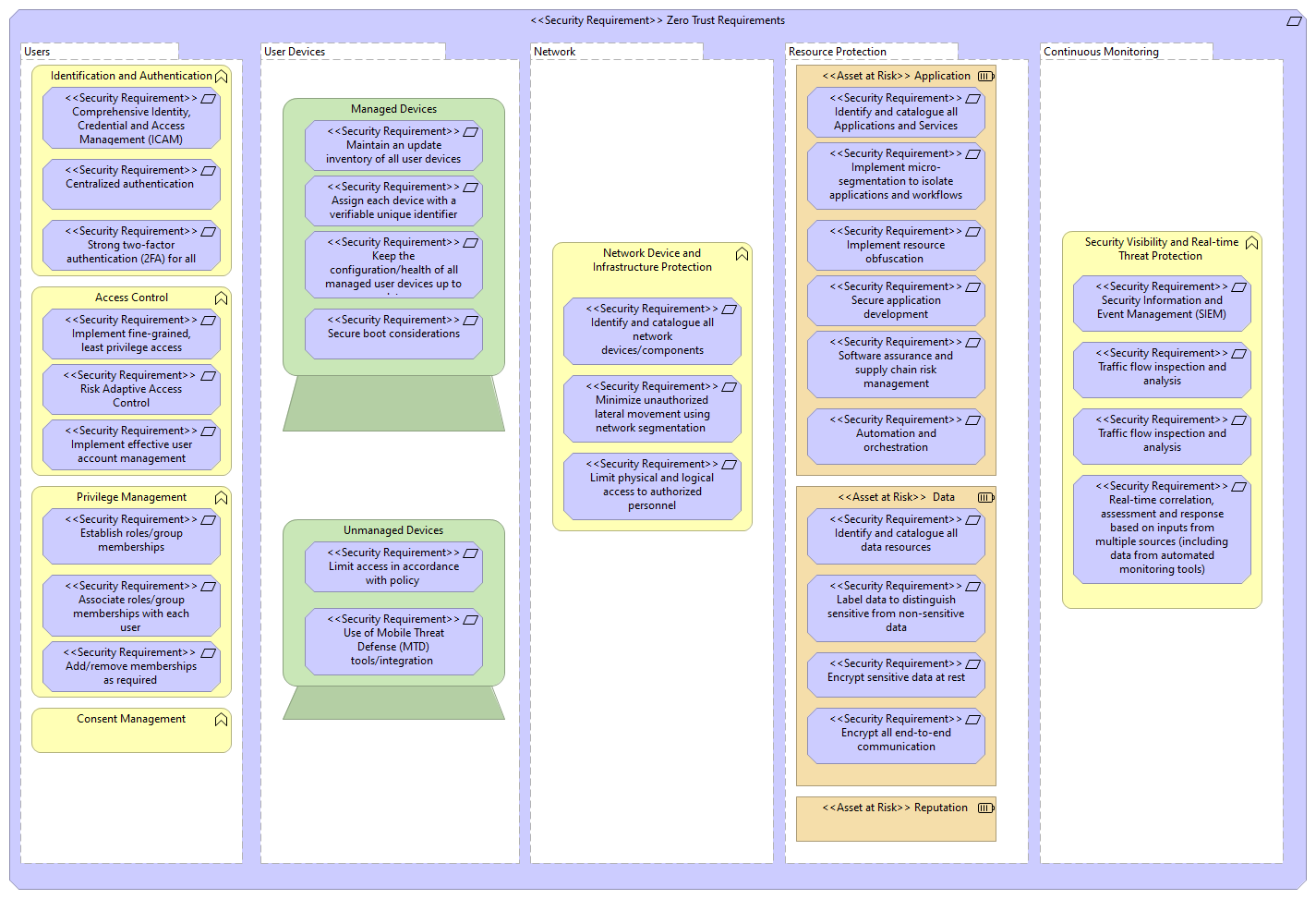
<<Security Requirement>> Zero Trust Requirements |
Resource Protection |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Continuous Monitoring |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Users |
| |
|
<<Security Requirement>> Zero Trust Requirements |
Network |
| |
|
<<Security Requirement>> Zero Trust Requirements |
User Devices |
| |
|
Resource Protection |
<<Asset at Risk>> Application |
| |
|
Resource Protection |
<<Asset at Risk>> Reputation |
| |
|
Resource Protection |
<<Asset at Risk>> Data |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Encrypt all end-to-end communication |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Label data to distinguish sensitive from non-sensitive data |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Encrypt sensitive data at rest |
| |
|
<<Asset at Risk>> Data |
<<Security Requirement>> Identify and catalogue all data resources |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Implement micro-segmentation to isolate applications and workflows |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Implement resource obfuscation |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Secure application development |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Identify and catalogue all Applications and Services |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Software assurance and supply chain risk management |
| |
|
<<Asset at Risk>> Application |
<<Security Requirement>> Automation and orchestration |
| |
|
Continuous Monitoring |
Security Visibility and Real-time Threat Protection |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Traffic flow inspection and analysis |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Security Information and Event Management (SIEM) |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Traffic flow inspection and analysis |
| |
|
Security Visibility and Real-time Threat Protection |
<<Security Requirement>> Real-time correlation, assessment and response based on inputs from multiple sources (including data from automated monitoring tools) |
| |
|
Users |
Identification and Authentication |
| |
|
Users |
Privilege Management |
| |
|
Users |
Access Control |
| |
|
Users |
Consent Management |
| |
|
Identification and Authentication |
<<Security Requirement>> Centralized authentication |
| |
|
Identification and Authentication |
<<Security Requirement>> Comprehensive Identity, Credential and Access Management (ICAM) |
| |
|
Identification and Authentication |
<<Security Requirement>> Strong two-factor authentication (2FA) for all users, regardless of location |
| |
|
Privilege Management |
<<Security Requirement>> Associate roles/group memberships with each user |
| |
|
Privilege Management |
<<Security Requirement>> Establish roles/group memberships |
| |
|
Privilege Management |
<<Security Requirement>> Add/remove memberships as required |
| |
|
Access Control |
<<Security Requirement>> Implement fine-grained, least privilege access control |
| |
|
Access Control |
<<Security Requirement>> Implement effective user account management procedures |
| |
|
Access Control |
<<Security Requirement>> Risk Adaptive Access Control |
| |
|
Network |
Network Device and Infrastructure Protection |
| |
|
Network Device and Infrastructure Protection |
<<Security Requirement>> Minimize unauthorized lateral movement using network segmentation |
| |
|
Network Device and Infrastructure Protection |
<<Security Requirement>> Limit physical and logical access to authorized personnel |
| |
|
Network Device and Infrastructure Protection |
<<Security Requirement>> Identify and catalogue all network devices/components |
| |
|
User Devices |
Managed Devices |
| |
|
User Devices |
Unmanaged Devices |
| |
|
Managed Devices |
<<Security Requirement>> Maintain an update inventory of all user devices |
| |
|
Managed Devices |
<<Security Requirement>> Secure boot considerations |
| |
|
Managed Devices |
<<Security Requirement>> Assign each device with a verifiable unique identifier |
| |
|
Managed Devices |
<<Security Requirement>> Keep the configuration/health of all managed user devices up to date |
| |
|
Unmanaged Devices |
<<Security Requirement>> Limit access in accordance with policy |
| |
|
Unmanaged Devices |
<<Security Requirement>> Use of Mobile Threat Defense (MTD) tools/integration |